Risk 360 is our intelligent platform for cyber risk identification & management
Risk 360 is our complete platform and risk management engine which can be used to identify, prioritise and remediate cyber security risks in your business operations.
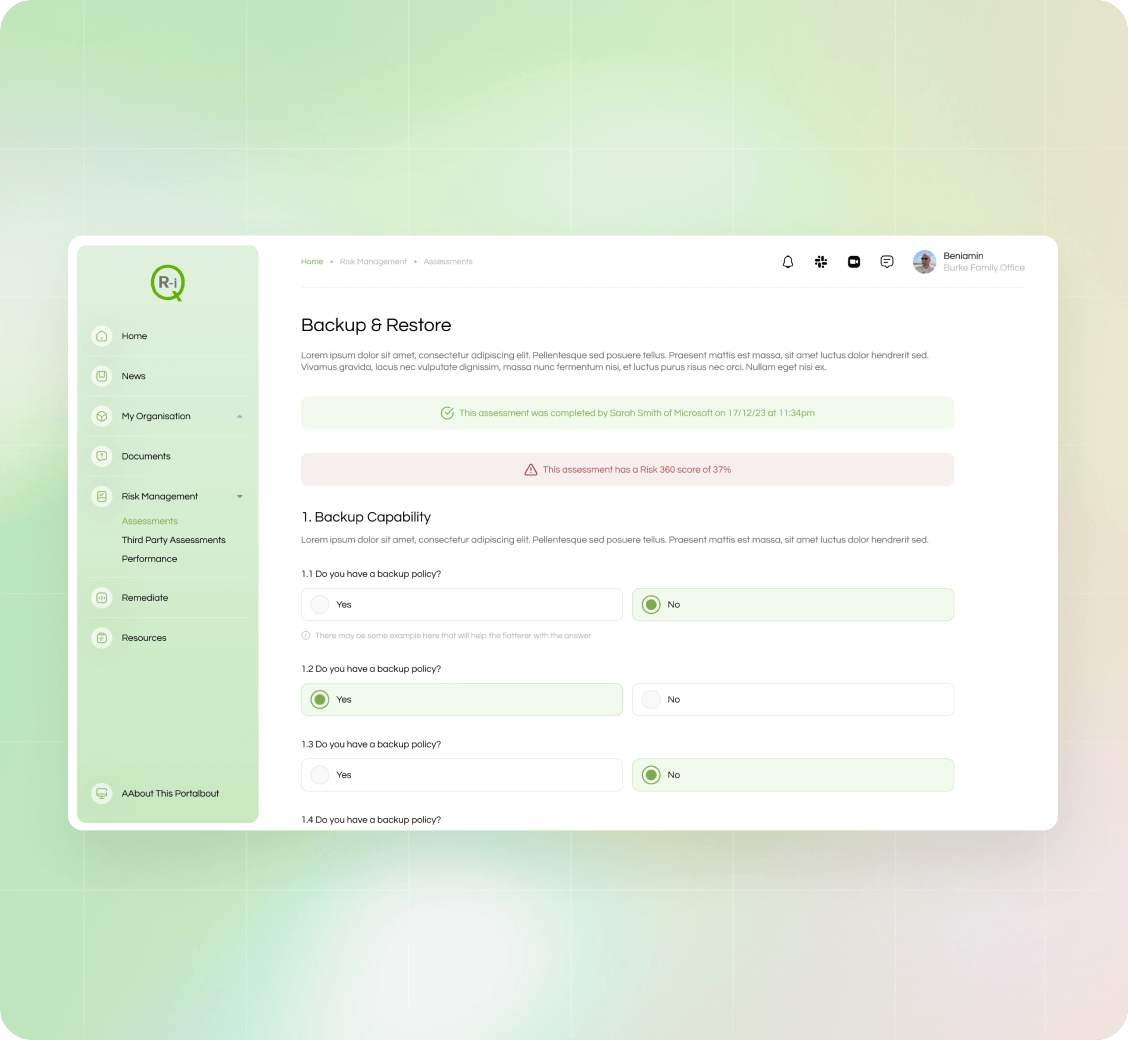
Holistic Risk Assessment
During discovery, we use Risk 360 to execute a number of assessments that enable us to holistically understand your current security practices and capability.
Our assessments span industry frameworks such as Cyber Essentials and SOC2 together with our suite of proprietary assessments which fully assess your organisations people, process and technology readiness.
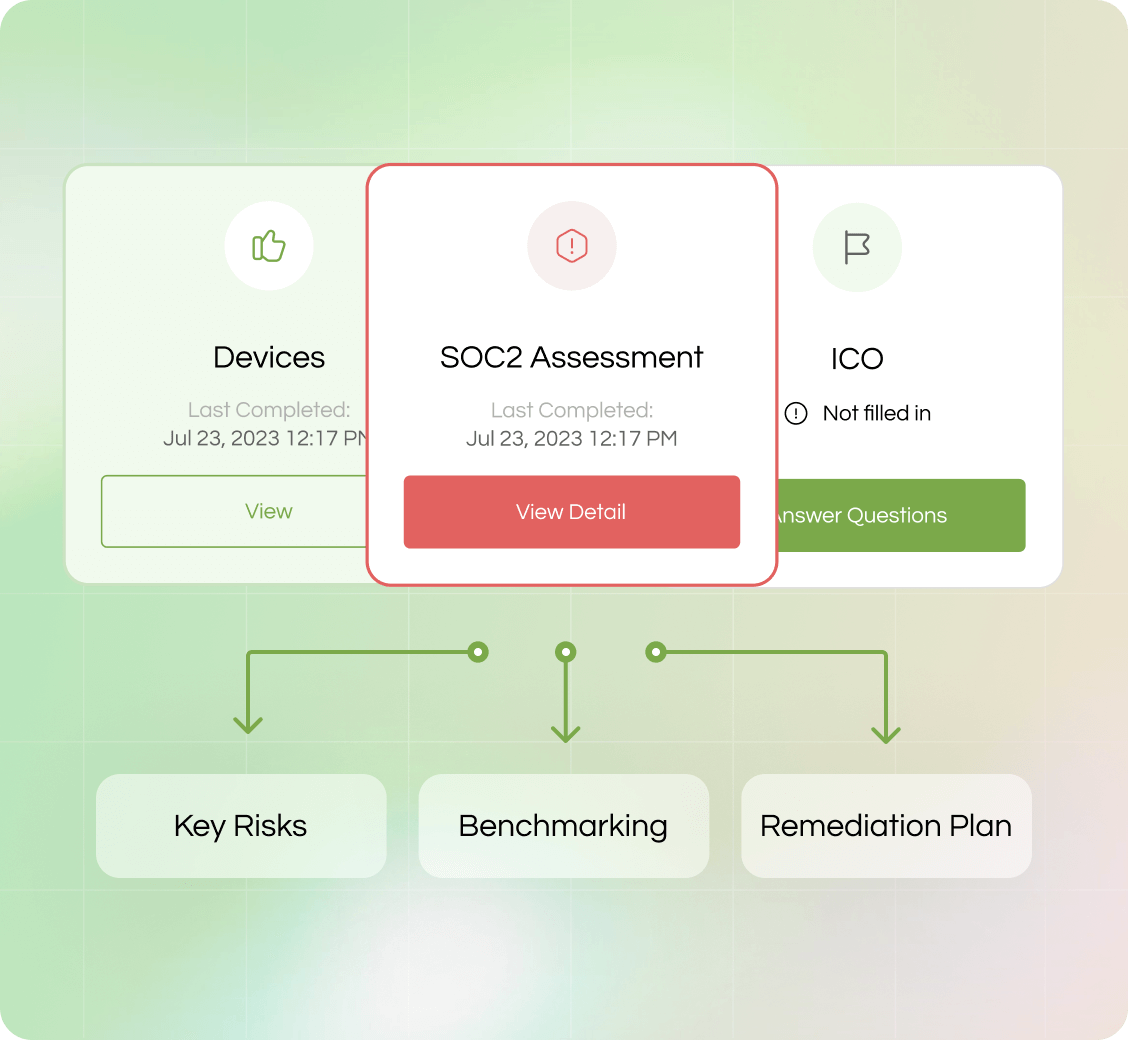
Automated Analysis
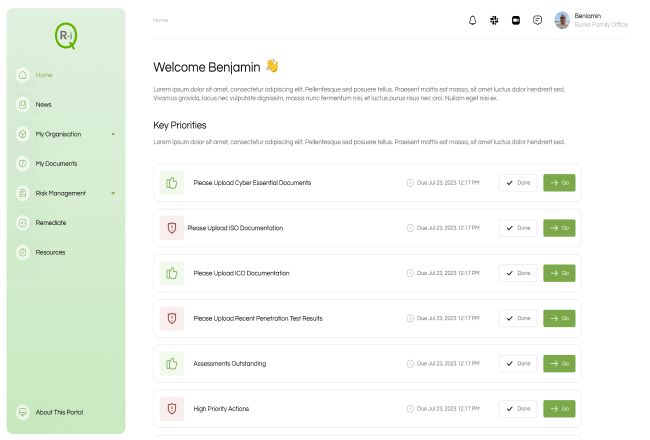
Risk 360 automatically analyses these assessments to identify key risks, benchmark your current maturity and propose a suggested remediation plan.
We will continually monitor and prompt your people to assess the highest priority areas in order to achieve continuous compliance.
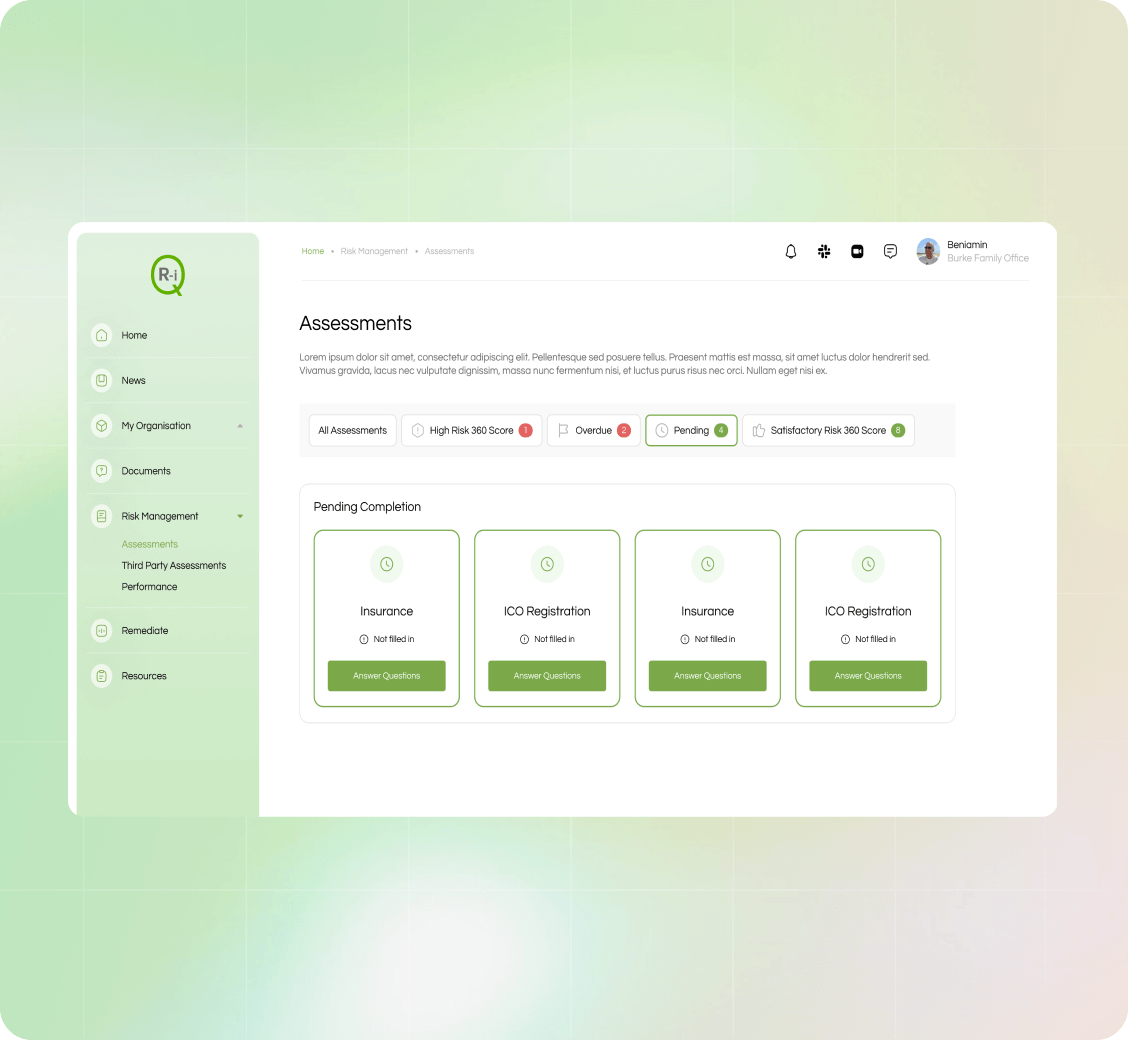
Risk Scoring Algorithm
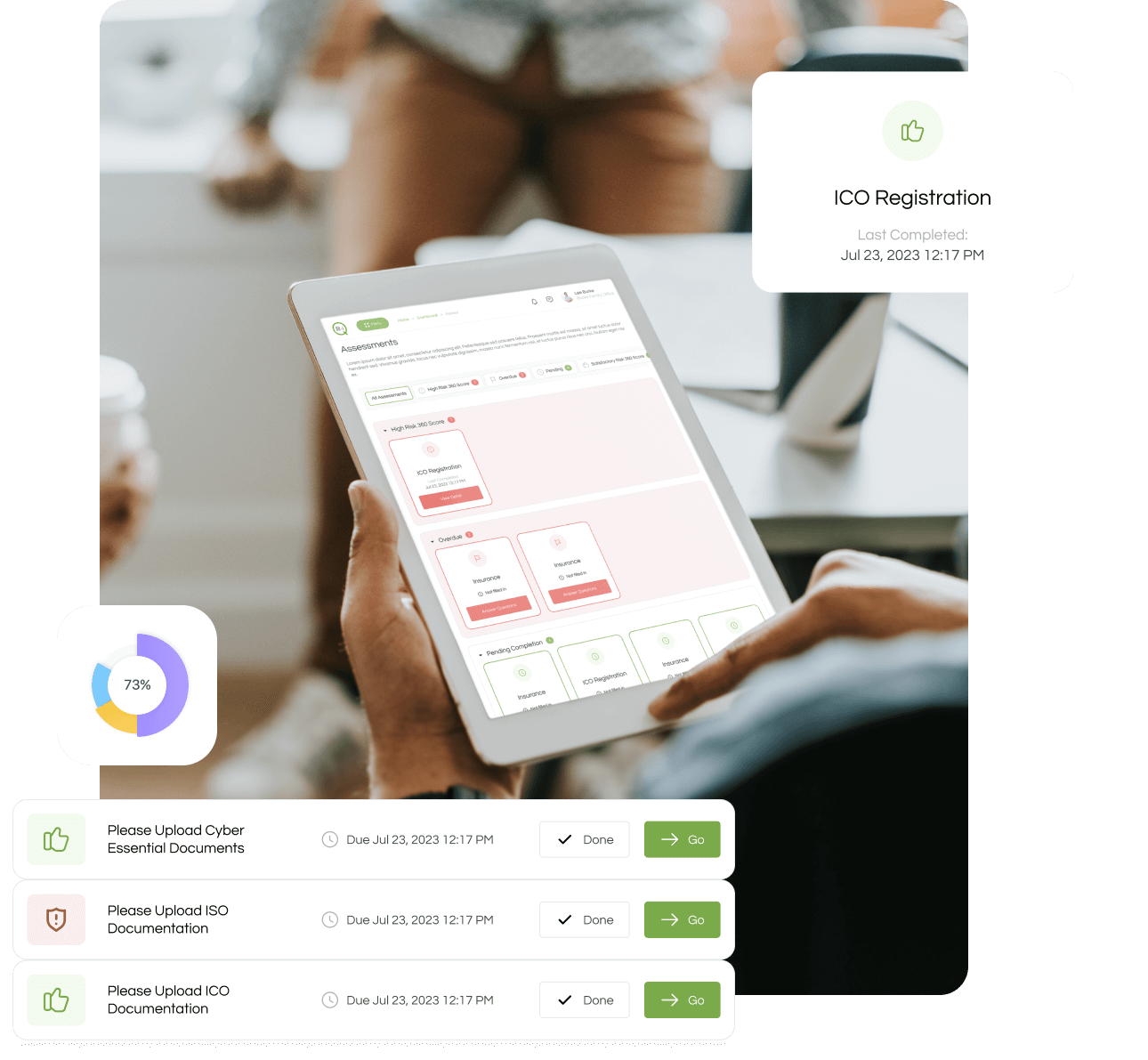
We have developed a proprietary scoring model and database which allows you to surface hidden risk, prioritise the highest impact items and identify exactly where the risk lies in your organisation.
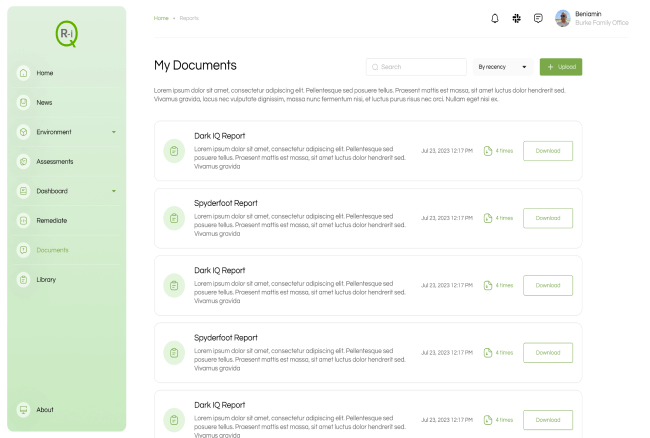
The results of these models are made available through easily consumable dashboards, metrics and risk logs.
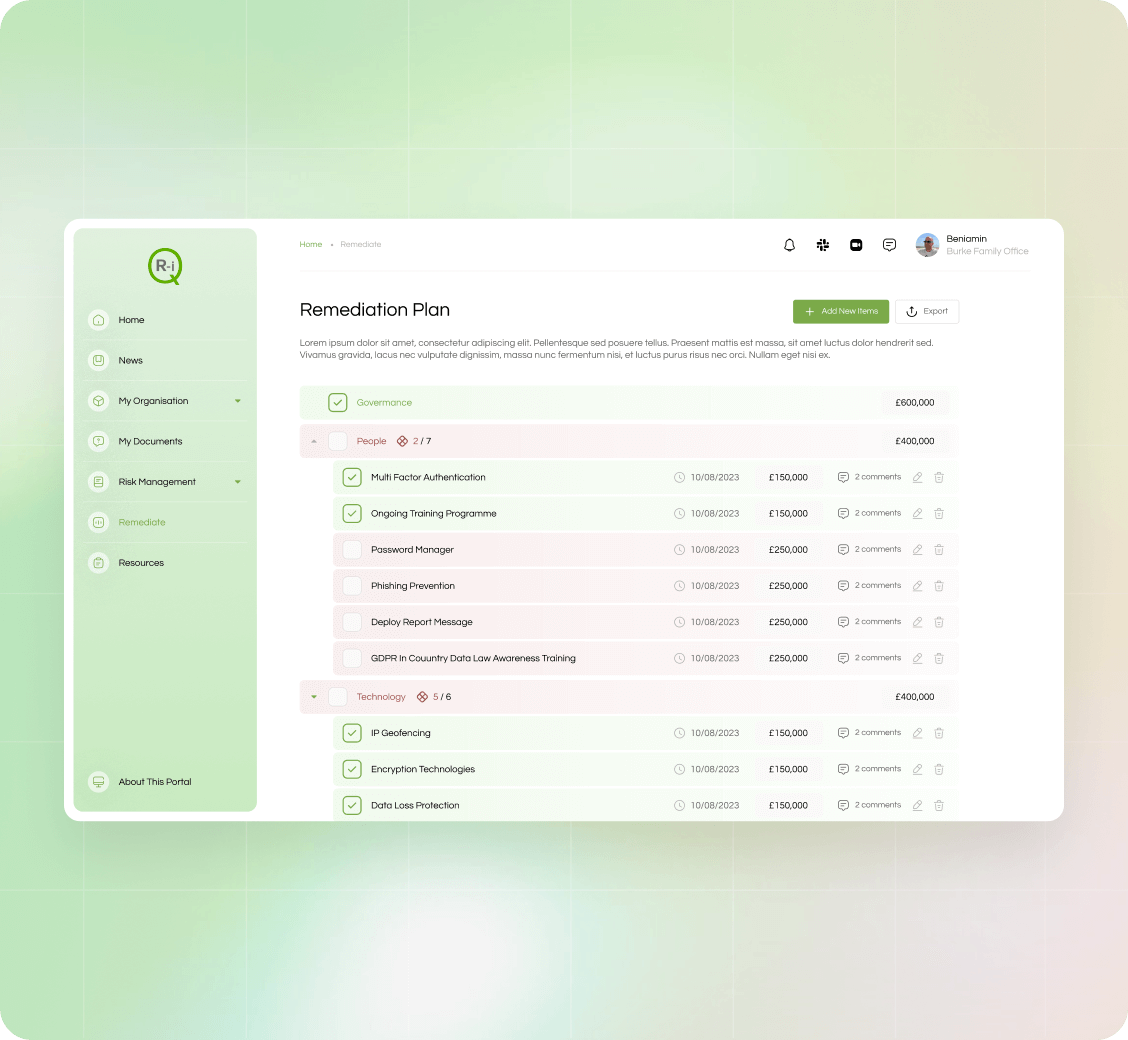
Remediation Process
Risk 360 will output a candidate remediation plan that offers a head start on how to close any security gaps. This would then typically be enhanced by your team and your advisors.
This remediation plan can be continually evolved and ued to support your ongoing remediation plan, acting as a single collaborative tool.
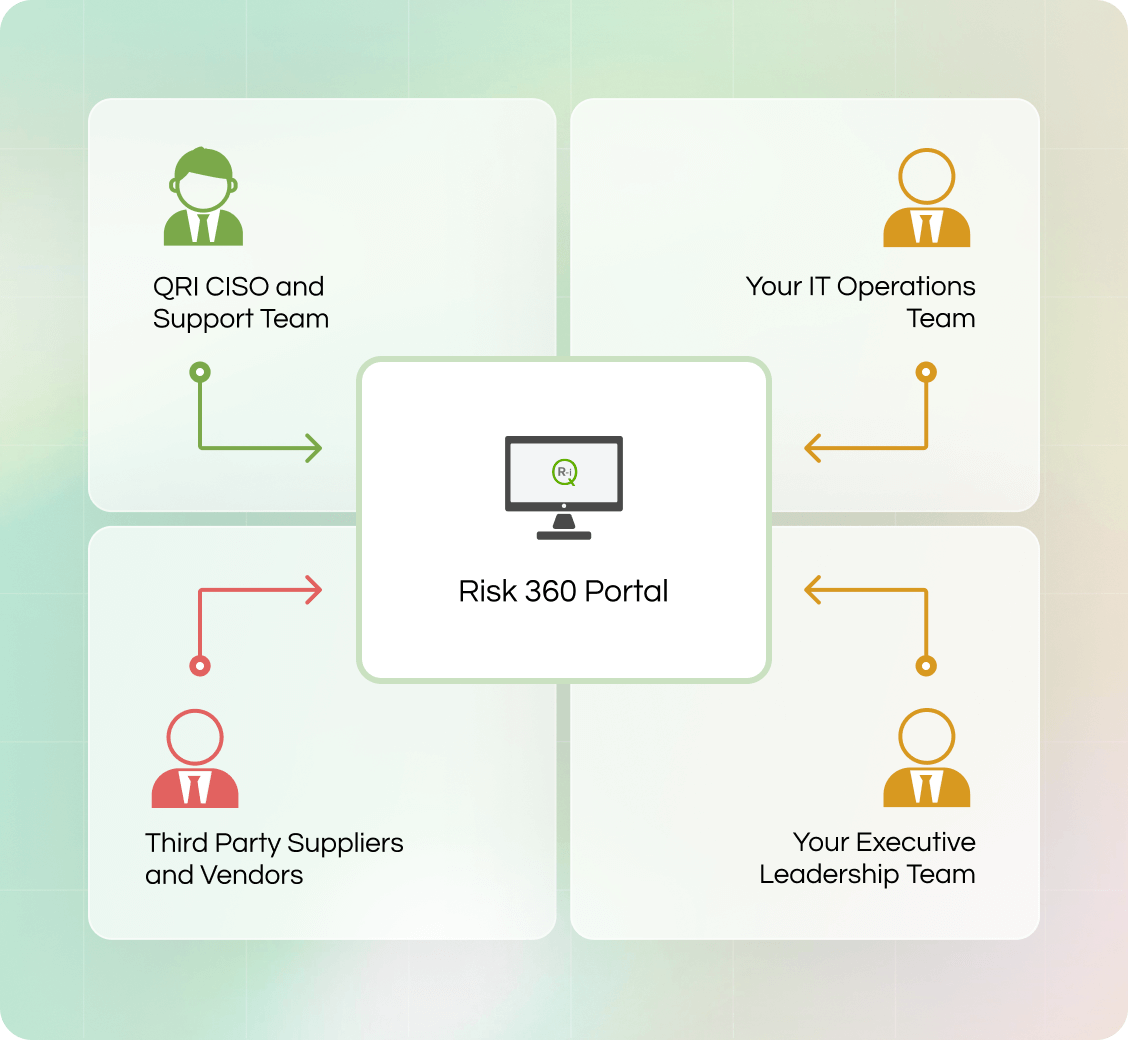
360 Collaboration
Risk 360 acts as a central collaboration point between all of the stakeholders involved in keeping your business secure.
This involves your IT security professionals, but also your executives and the third party vendors and partners that serve your organisation.
This is a key point of differentation as most cyber security tooling is technically focussed and siloed.
Continuous Compliance
The process outlined above is continually executed, ensuring that your business remains secure and that a full picture of your organisations readiness and capability is always captured.
Executive Visibility
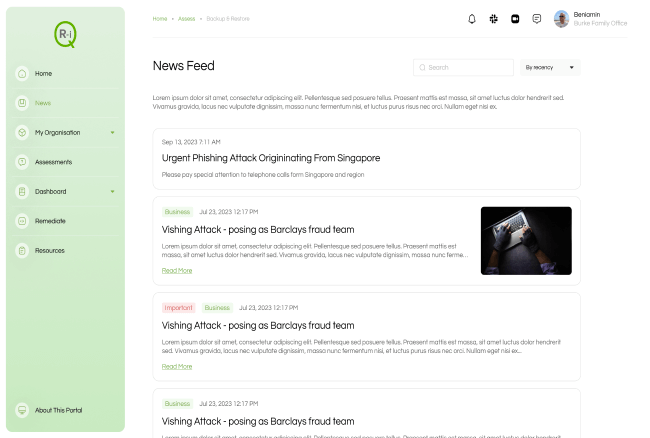
Risk 360 surfaces security risks from your on-the-ground operational activity and presents it in a summarised format suitable for executives.
Risk360 exposes any risks to executives via a dedicated web experience and mobile application. These risks are described in an easy to consume risk log and through high level dashboards.
As your organisation is continually being assessed, any changes in this picture and over all risk posture are alerted to the executive promptly.
Third Party Risk
If your third party vendors and partners are not secure, then neither are you. We've therefore bought third party vendors into the same collaborative platform.
Assess Third Party Dependencies
If your third party vendors and partners are not secure then neither are you. Considering this, we enable third party due diligence assessments which are processed by the same risk management and scoring engine.

Remediation Tasks
We use the portal to surface and manage your remediation programme as it progresses with full transparency to all stakeholders.
Other Features
We use Risk 360 to proactively work with your organisation to continually improve your security posture.